Context through Metadata: Increasing understanding and trust in photo journalism through HCI
The oft-used idiom “A picture is worth a thousand words” – meaning that a single image can communicate a complex idea or message – is hard to dispute. We are surrounded by visual media in modern society: it is prominent in everything from advertising and entertainment to scientific journals and documentation. Images, arguably even more so than mathematics, exist as a universal language which transcends more cultural, literacy and age barriers than any other. The rise of HCI has only increased their prevalence – images are now distributed to millions through online social networks and communities and, thanks to smartphones, they can not only be accessed anywhere at any time, but also produced and shared effortlessly. In the age of selfies, Tweets limited to 140 characters, mobile broadband, busy lifestyles and short attention spans, visual media has become more important and influential than ever.
However, not everything is peachy. With wider access to image manipulation software, images are increasingly easy to doctor. Not only that, even unaltered images can be taken out of context, with unexpected and unwanted consequences. As a result of these factors it can sometimes be difficult for consumers to trust the images they view. This is of particular concern in journalism, where accuracy is of the utmost importance and without the audience’s trust the profession is meaningless. I argue that a lack of trust in journalism would inevitably result in a lack of trust in democracy, as the two are intrinsically linked. As local democracy is one of the core pillars of the Digital Civics programme, the issue seems especially relevant. In this blog post I will be exploring examples where a lack of context behind images has led to unintended consequences, and suggesting ways in which we can use the various fields of HCI we have investigated (such as online communities, ubiquitous computing and big data) alongside new, novel technologies such as the Bitcoin block chain to combat the issue.
Exploring the Problem
 As stated earlier, an image doesn’t have to be manipulated to give inaccurate (or unintended) messages to those who view it. One of the most noteworthy instances of this was Eddie Adams’ photograph “Saigon Execution”, which showed General Nguyễn Ngọc Loan executing a Vietcong prisoner, Nguyễn Văn Lém during the Vietnam War. The photo won Adams the Pulitzer Prize, however he came to lament its notoriety. It became synonymous with the Tet Offensive, destroying the General’s career and was a PR catastrophe for the US war effort. In Time magazine in 1998, Adams wrote:
As stated earlier, an image doesn’t have to be manipulated to give inaccurate (or unintended) messages to those who view it. One of the most noteworthy instances of this was Eddie Adams’ photograph “Saigon Execution”, which showed General Nguyễn Ngọc Loan executing a Vietcong prisoner, Nguyễn Văn Lém during the Vietnam War. The photo won Adams the Pulitzer Prize, however he came to lament its notoriety. It became synonymous with the Tet Offensive, destroying the General’s career and was a PR catastrophe for the US war effort. In Time magazine in 1998, Adams wrote:
“The general killed the Viet Cong; I killed the general with my camera. Still photographs are the most powerful weapons in the world. People believe them; but photographs do lie, even without manipulation” [1]
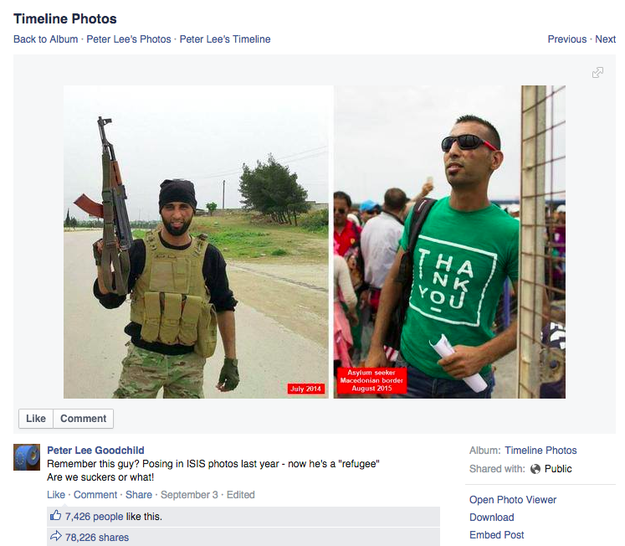
Today, instances such as this are more visible than ever due to a lack of fact-checking and the prevalence of online communities. Images and video lacking context (or worse, having been given the wrong context) can “go viral” and spread misinformation or unintended messages to millions. One prominent example in 2015 was an image featuring two photographs of a man who has now been identified as Laith al-Saleh. The first photograph showed him in military garb, brandishing an AK-47 assault rifle; the second, him amongst a group of civilians wearing a T-shirt saying “thank-you”. The image was shared to Facebook, with the caption “Remember this guy? Posing in ISIS photos last year – now he’s a ‘refugee’. Are we suckers or what!”
In truth, Laith al-Saleh is a former commander of the Free Syrian Army, a group of rebels who oppose and fought both the Syrian President Al-Assad and ISIS, the group he was accused of being a member of. Talking to the Associated Press about the Syrian migrants only a month earlier, he said:
“Everyone wants to leave Syria. My (home) is the most dangerous city in the world. About 70 percent of the city is destroyed… In Syria, Al Qaeda want me, Daesh (ISIS), the government — I fought them all. [2]
While the author of the post later apologised, the image and its accusations had already been shared by at least 80,000 Facebook members. [3]

Another widely shared example from 2015 was a photograph of two children holding each other – purportedly victims of the recent earthquake in Nepal. However, the photographer (Na Son Nguyen) revealed that the photograph was taken in Vietnam eight years earlier, and had been shared out of context. [4]
It’s clear, then, that in many situations a note of authenticity and an additional source of context would be useful. If Eddie Adams was able to give additional information to those who had seen Saigon Execution regarding the prisoner’s crimes, perhaps the public would have reacted to it differently. Additional explanation of who Al-Saleh was fighting may have prevented his Facebook smearing. With the increased availability of image manipulation software, users can also often be left in doubt as to whether or not the image they’re presented has been tampered with.
What can be done?
To encourage trust and accuracy in journalists’ images we must at least establish three things: First, the context surrounding the capture of the image; Second, that the viewed image is the same that the journalist produced; Third, that this additional information can be authored and consumed quickly and easily.
Building Images’ Context
The audience’s misunderstanding of images can be countered by simply providing more information. Information regarding the shot’s location, date and time and the identity of the photographer are usually already stored in the image’s standard EXIF data. While the promotion of this data would certainly solve some discrepancies (such as the ‘Nepal earthquake’ siblings) it doesn’t help convey more complex ideas. Again, there is a section in the EXIF data for freeform text, allowing the photographer to state their intentions and their interpretation of events.
Building and Utilising Online Communities
 However, interpretations and perspectives could also be submitted by others. Mirroring recent design patterns within HCI, we should be critical of whether or not the photographer knows the image’s subject better than the viewer. Allowing experts within online communities to freely contribute to an amalgamation of knowledge has proven extremely successful in the past, as shown in projects such as Wikipedia. Harnessing “the wisdom of the crowd” not only allows for greater transparency (which arguably would lead to greater levels of trust) and a variety of viewpoints (allowing more opinions to be represented), but would also potentially allow for information to be kept up to date over time, without relying on the original image’s author for maintenance of data. Of course before any of this can happen, the factors behind successful online communities (and the reasons for the failure of those which have collapsed) must be first understood. Iriberri and Leroy’s “Online Community Lifecycle” outlines a clear set of stages that online communities tend to adhere to: Inception, which requires the need for a community and a vision for it; Creation, requiring technology resources and initial, purposeful community members; Growth, during which roles form within the community and rules are set in place; Maturity, which is a cyclical stage during which relationships are built, bonds of trust are established and subgroups formed; and finally Death. Iriberri and Leroy identify that a lack of contribution, participation or content can lead to the ‘death’ of an online community. [5] As Stuart pointed out in his blog post on the same paper [6], another contributing factor to the death of a community could be the rise of a rival one which fulfils a similar purpose in a more successful manner – an issue which has plagued social networks in the past (e.g. Bebo and Myspace). It may be important to note, however, what Iriberri and Leroy class are using as a success metric for these communities. While they might label a community with a low population as a failure, if that population is producing appreciable amounts of worthwhile content we might class it as a success.
However, interpretations and perspectives could also be submitted by others. Mirroring recent design patterns within HCI, we should be critical of whether or not the photographer knows the image’s subject better than the viewer. Allowing experts within online communities to freely contribute to an amalgamation of knowledge has proven extremely successful in the past, as shown in projects such as Wikipedia. Harnessing “the wisdom of the crowd” not only allows for greater transparency (which arguably would lead to greater levels of trust) and a variety of viewpoints (allowing more opinions to be represented), but would also potentially allow for information to be kept up to date over time, without relying on the original image’s author for maintenance of data. Of course before any of this can happen, the factors behind successful online communities (and the reasons for the failure of those which have collapsed) must be first understood. Iriberri and Leroy’s “Online Community Lifecycle” outlines a clear set of stages that online communities tend to adhere to: Inception, which requires the need for a community and a vision for it; Creation, requiring technology resources and initial, purposeful community members; Growth, during which roles form within the community and rules are set in place; Maturity, which is a cyclical stage during which relationships are built, bonds of trust are established and subgroups formed; and finally Death. Iriberri and Leroy identify that a lack of contribution, participation or content can lead to the ‘death’ of an online community. [5] As Stuart pointed out in his blog post on the same paper [6], another contributing factor to the death of a community could be the rise of a rival one which fulfils a similar purpose in a more successful manner – an issue which has plagued social networks in the past (e.g. Bebo and Myspace). It may be important to note, however, what Iriberri and Leroy class are using as a success metric for these communities. While they might label a community with a low population as a failure, if that population is producing appreciable amounts of worthwhile content we might class it as a success.
Because the potential subject matter of journalist-produced images is extremely broad, it would almost certainly overlap with communities which focused on more specific niches. The study of Zhu et al. into identifying niches for creating successful online communities noted that many communities failed to gain momentum because of this – too large of a content overlap with other communities resulted in decreased user activity. However, they also found that communities which linked to those which they overlapped with showed increased activity, along with increased learning and content sharing. [7] This could potentially be utilized to the mutual benefit of both this new, overarching community (which potentially gains expert niche knowledge) and the smaller, focused ones (which may benefit from more exposure). This can be seen in some websites such as Reddit, where small sub-communities (aka subreddits) co-exist with the much larger, all-encompassing Reddit community in a symbiotic relationship.
Adding Context through Ubiquitous Computing, Machine Learning and Big Data
While true insight into a subject might only be provided through human input, large amounts of information can be contributed autonomously. Weiser’s vision of ubiquitous computing – as outlined in his seminal paper The Computer for the 21st Century [8] – is arguably starting to finally be a reality. The increasing market share of smartphones thanks to rapidly falling price tags and the widespread belief that Internet access is a fundamental right – amongst other factors – point towards the fact that we’re finally entering Bell and Dourish’s “proximate future”. [9] I have discussed this issue in a previous blog post, examining their paper “Yesterday’s Tomorrows”. [10]
The personal computing devices we use are more interconnected than ever and our identities, social connections, lifestyles and relationships are omnipresent – available anywhere at any time. With such a rich tapestry of data available, the data that we choose to transport alongside our images seems surprisingly limited. Say you’re going out for a meal with friends and take a photograph – why is your mobile phone only able to tag your GPS location in a taken photo’s metadata, when it likely has access to so much more? It would almost certainly be able to retrieve the name of the restaurant, and likely would be able to access the food menu. Through a combination of recognised Bluetooth devices, facial recognition, your social network’s events schedule and group chat, it could access who was at the meal (and who was conspicuously absent). It could use your movements and data from your online fitness tracking profile to determine that you’d pre-emptively exercised beforehand. By comparing your walking pattern to your usual using the accelerometer, it could probably determine that you’ve had a bit too much to drink (as well as comparing the restaurant’s drinks menu with a little image recognition to take a decent stab at your poison of choice). This is obviously an extreme example which many people would be uncomfortable with, but it’s interesting that in today’s data-obsessed society this kind of functionality isn’t offered when producing images on modern devices. Some services do, however, offer features which give images a bit more context by utilising the image’s existing metadata in combination with their own datasets.
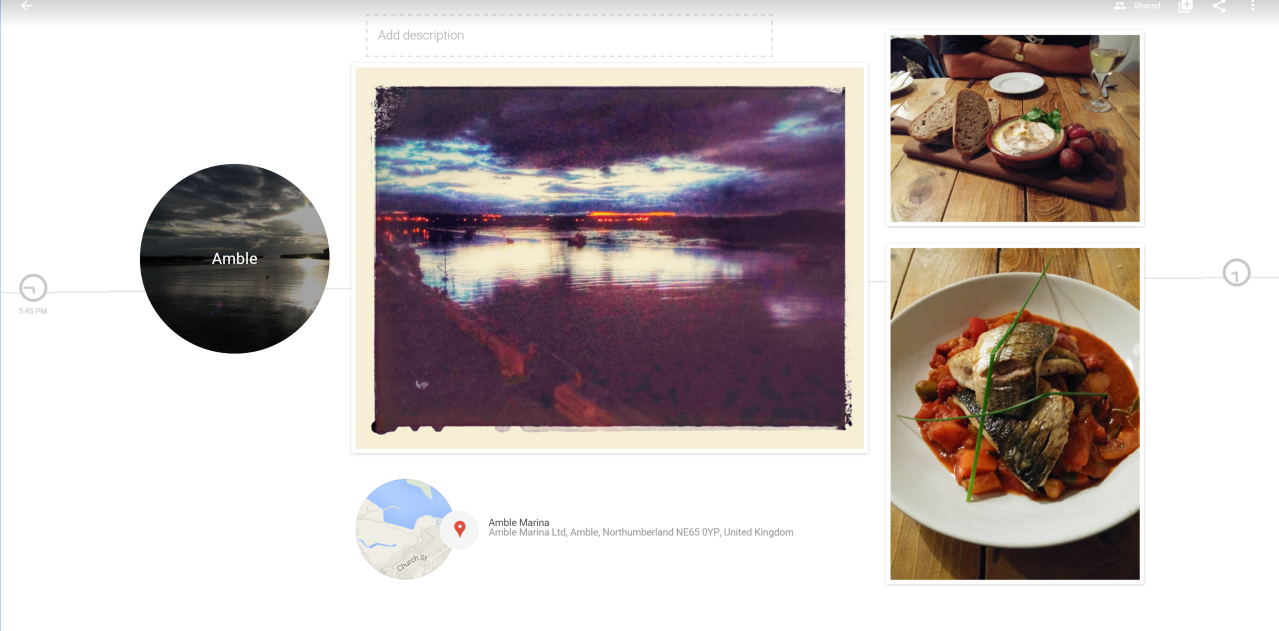
When users upload albums of images to the Google Photos service (above), the application uses the images’ EXIF data to produce “stories”. The photos’ date and time are used in conjunction with location data to intelligently infer context – the above example is from a story automatically labelled “Weekend in Northumberland”. The service used these photos’ GPS locations in combination with the Google Places API to determine that we visited Amble Marina, although it didn’t manage to identify that we had eaten dinner at a nearby restaurant. Machine learning algorithms are also applied, identifying who and what is visible in each image to allow the user to “semantic search”. Users are invited to add their own comments to the story during its progression, so that it doesn’t rely on data generation alone. Services such as Google Photos are getting closer to our imagined restaurant scenario, but they’re propriety and don’t store the collected data inside the image file in a standard way. However, it’s easy to see how these approaches can improve a user’s understanding of an image’s content.
Reassuring the viewer that the image is the author’s
A lot of work has been done to try and detect when images have been manipulated, often involving analysing the image for inconsistencies in elements such as shadows and reflections. However, often the author will simply require proof that they were in possession of the image at a certain point in time (for example, Na Son Nguyen proving that his photograph existed in 2007). The BitCoin block chain has been shown to be an extremely suitable vehicle for this “proof of existence” – by creating a cryptographic hash of the image and then including it in a BitCoin transaction (which gets stored permanently in the block chain), the author can provide irrefutable proof that they had that exact image in their possession at the time of the transaction. [11] If the image has been tampered with in any way, the resulting cryptographic hash will be different to the one in the block chain, proving it is altered. This functionality could also be applied to many forms which may require proof, from legal documents such as wills to purchase receipts.
Creating useful systems and usable interfaces through diverse design techniques
 People will not use a product or service I have encountered multiple participatory design processes over the course of the HCI module. Participatory design is a particularly useful approach to follow, as it attempts to involve as many of the product’s stakeholders in the design process as possible, helping ensure that the end result is usable and meets their needs. One of the more unusual and interesting design methods was “experience design theatre” (EDT) – a technique of exploring future scenarios, using professional actors to play out situations and adapt to participants’ interactions and suggestions. [12] EDT is an unusual form of a prototyping workshop, with the imaginary end product evolving according to feedback and criticism. Participants are encouraged to provide feedback during the performance, meaning that it could be immediately adapted according to the participants’ suggestions and re-enacted. This “re-direction” of scenes provides immediate feedback for the participants, which is something that many other types of workshop might lack. [13] This could be extremely useful when designing a feature set for a project such as this – a hugely broad array of situations could occur when taking a photo, and many participants would have different needs of what data would be of interest in different situations. Exploring a scenario and adapting it according to participant feedback would allow for a better equipped final design. This technique would be useful for exploring what participants think the weaknesses of the current state of the medium of photography are, gauging reactions to more intelligent data collection and investigating what people want to get out of their previously taken photos when going through them. Using EDT as a prototyping tool is especially useful, as the ‘designs’ can be altered immediately upon participant feedback – meaning that if participants react negatively to a higher level of data collection, for example, it can be dialled back and reassessed straightaway.
People will not use a product or service I have encountered multiple participatory design processes over the course of the HCI module. Participatory design is a particularly useful approach to follow, as it attempts to involve as many of the product’s stakeholders in the design process as possible, helping ensure that the end result is usable and meets their needs. One of the more unusual and interesting design methods was “experience design theatre” (EDT) – a technique of exploring future scenarios, using professional actors to play out situations and adapt to participants’ interactions and suggestions. [12] EDT is an unusual form of a prototyping workshop, with the imaginary end product evolving according to feedback and criticism. Participants are encouraged to provide feedback during the performance, meaning that it could be immediately adapted according to the participants’ suggestions and re-enacted. This “re-direction” of scenes provides immediate feedback for the participants, which is something that many other types of workshop might lack. [13] This could be extremely useful when designing a feature set for a project such as this – a hugely broad array of situations could occur when taking a photo, and many participants would have different needs of what data would be of interest in different situations. Exploring a scenario and adapting it according to participant feedback would allow for a better equipped final design. This technique would be useful for exploring what participants think the weaknesses of the current state of the medium of photography are, gauging reactions to more intelligent data collection and investigating what people want to get out of their previously taken photos when going through them. Using EDT as a prototyping tool is especially useful, as the ‘designs’ can be altered immediately upon participant feedback – meaning that if participants react negatively to a higher level of data collection, for example, it can be dialled back and reassessed straightaway.
Design fiction would be another interesting method to utilise in this area, creating a critical design to challenge the accepted role of images, image viewers and photographers in society. Design fiction can be quite effective and thought provoking, especially if used with a straight face. In a previous blog post [14] I looked at the paper ‘Fit4Life’ by Purpura et al [15], where they put forward a satirical critical design for a persuasive technology which used extreme persuasive computing methods and data tracking to ‘help’ its users lose weight. The first half of the paper is played completely straight, without an acknowledgement that Fit4Life is actually a fictional, critical design. By doing this, the authors claimed that readers would have to begin critically questioning the design themselves, rather than be complacent due to knowing it to be fictional. However, the design became increasingly outrageous as it is revealed (culminating in the HAL 9000-esque “I’m sorry, Dave, you shouldn’t eat that”) meaning that even the most oblivious of readers were likely to recognise the satirical tone. The extreme examples of data tracking and persuasive techniques were used to provoke readers into reflecting on when design goes too far. This would be an interesting approach to apply to contextual data collection in photography – examples such as our earlier hypothetical restaurant scenario may be seen to be outrageous, but by presenting it as an existing product à la Fit4Life we can explore the boundaries of acceptability.
Final Words
Through this post I hope to have shown that the lack of context that often comes alongside images can have extremely harmful effects, and that this issue seems to be becoming more prevalent thanks to images’ rapid propagation across the Internet. We’ve seen that this can be especially damaging in photo journalism – due to how the subject matter can often be sensitive or divisive – and could potentially lead to citizens lacking trust in journalists’ content, negatively impacting democracy. We’ve also touched upon a few potential avenues through which Digital Civics researchers could explore possible solutions, along with some design techniques which would help elevate users into the role of designers through participatory design.
In my future work in Digital Civics I would like to attempt to put these ideas into practice and investigate related issues. Can communities be relied upon to collaborate and create high quality, accurate content? Could a community be self-sufficient, or would a degree of editing/organising be required? What kind of additional contextual information would be most valued by consumers, and would this help solidify their trust in an image? I would also be interested in seeing if this additional context could be used for educational purposes, combining multiple communities’ expertise to spread knowledge.
References
| [1] | Adams, “Eulogy: GENERAL NGUYEN NGOC LOAN,” Time Magazine, 27 July 1998. [Online]. Available: http://content.time.com/time/magazine/article/0,9171,988783,00.html. [Accessed 5 January 2016]. |
| [2] | Paphitis and D. Bennett, “Syrian rebel leader seeks Europe, fleeing gov’t and jihadis,” 17 August 2015. [Online]. Available: http://news.yahoo.com/syrian-rebel-leader-seeks-europe-fleeing-govt-jihadis-163636165.html. [Accessed 5 January 2016]. |
| [3] | Wendling, “This viral photo falsely claims to show an IS fighter posing as a refugee,” BBC News, 07 September 2015. [Online]. Available: http://www.bbc.co.uk/news/blogs-trending-34176631. [Accessed 5 January 2016]. |
| [4] | Rusk, “How the internet misled you in 2015,” BBC News, 27 December 2015. [Online]. Available: http://www.bbc.co.uk/news/world-35051618. [Accessed 5 January 2016]. |
| [5] | Iriberri and G. Leroy, “A life-cycle perspective on online community success,” 2009. |
| [6] | Nicholson, “Stuart Nicholson – A life-cycle perspective on online community success,” HCI for Digital Civics 2015, 1 November 2015. [Online]. Available: https://openlab.ncl.ac.uk/hci-digitalcivics-2015/stuart-nicholson-a-life-cycle-perspective-on-online-community-success/. [Accessed 6 January 2016]. |
| [7] | Zhu, J. Chen, T. Matthews, A. Pal, H. Badenes and R. E. Kraut, “Selecting an effective niche: an ecological view of the success of online communities,” 2014. |
| [8] | Weiser, “The computer for the 21st century,” 1991. |
| [9] | Bell and P. Dourish, “Yesterday’s tomorrows: notes on ubiquitous computing’s dominant vision,” 2006. |
| [10] | Richardson, “Dan’s review of week 3 paper: “Yesterday’s Tomorrows: Notes on ubiquitous computing’s dominant vision”,” 26 October 2015. [Online]. Available: https://openlab.ncl.ac.uk/hci-digitalcivics-2015/dans-review-of-week-3-paper-yesterdays-tomorrows-notes-on-ubiquitous-computings-dominant-vision/. [Accessed 6 January 2016]. |
| [11] | Araoz, “Proof of Existence – About,” 2012. [Online]. Available: https://www.proofofexistence.com/about. [Accessed 6 January 2016]. |
| [12] | Richardson, “Experience Design Theatre: Just an act?,” 25 November 2015. [Online]. Available: https://openlab.ncl.ac.uk/hci-digitalcivics-2015/experience-design-theatre-just-an-act/. [Accessed 6 January 2016]. |
| [13] | Vines, T. Denman-Cleaver, P. Dunphy, P. Wright and P. Olivier, “Experience design theatre: exploring the role of live theatre in scaffolding design dialogues,” 2014. |
| [14] | Richardson, “I can’t let you eat that, Dave. Have some carrot juice instead.,” HCI for Digital Civics 2015, 2 December 2015. [Online]. Available: https://openlab.ncl.ac.uk/hci-digitalcivics-2015/i-cant-let-you-eat-that-dave-have-some-carrot-juice-instead/. [Accessed 7 January 2016]. |
| [15] | Purpura, V. Schwanda, K. Williams, W. Stubler and P. Sengers, “Fit4life: the design of a persuasive technology promoting healthy behavior and ideal weight,” 2011. |
Leave a Reply Cancel reply
You must be logged in to post a comment.